The modern battlespace is no longer merely guerrilla warfare. It’s the unknown cyber adversary that we cannot define that targets our most valuable infrastructures and seeks to harm our way of life. One of the challenges concerning our congressional leaders and front-line cybersecurity professionals is our cyber enemies’ unknown and ever-evolving capabilities.
The battlespace and the Soldiers have changed. As technology emerges, so have the world powers seated at the “executive table.” China in 2019 was the first country to send an unmanned rover to the far side of the moon. Today, we have self-driving cars and predictions that we could be landing the first human on Mars in less than five years. Technology is growing and maturing in unimaginable ways, so how do we secure ourselves within this ever-changing threatscape?
The top things to remember at a high level when thinking about the cybersecurity industry:
- Hackers are getting smarter
- Cybercrime is exploding (and it’s expensive for organizations)
- Automation is the future
- Vulnerabilities are endless
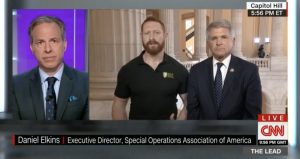
Daniel Elkins, the founder of the Special Operations Association of America, was recently interviewed on NewsMax Media, Inc. about China’s activities of possibly adding code to BIOs systems.
He addressed critical topics, which included the needed unconventional approach to battling this new and emerging warfare. The old school siloed approach to DoD cybersecurity must be addressed to allow effective collaboration among branches and combatant commands.
In 2020, the average cost for a large business data breach was more than $150 million. In 2019, the average breach was only around $3.92 million.
Daniel also touched on SolarWinds. This breach was the largest supply chain attack. Cyber professionals are unclear on the impacts this breach will have on our supply chain, and we may never fully comprehend and severity of this attack.
Another example of a recent, yet unsuccessful cyber attack, was the nefarious cyber activity that targeted the Florida water treatment plant. On February 9th, 2021 an adversary breached the industrial control system called Supervisory Control and Data Acquisition (SCADA) and began increasing sodium hydroxide in the water. The attack was prevented by an alert plant supervisor who spotted the change in the dosing amount.
It is uncertain at the time if this attack was conducted by a sophisticated state-threat group, script-kitty, or an insider threat. One of the workers quoted that they saw their mouse moving on the screen of the computer. This a rookie move and not typically seen from a state-threat group that is trying to go unnoticed. However, if a script-kitty breached the system, it is even more concerning that someone who is “unskilled” could gain this type of access.
Congressional leaders are in a tough spot in providing clear and concise cyber legislation because they don’t know what they don’t know. What we know today about cybersecurity could drastically change tomorrow because of a new breach or attack.
It wasn’t till the Computer Fraud and Abuse Act (CFAA) of 1984 that we saw any significant piece of legislation specific to cyber law. This law covered general crimes such as malicious damage to federal computer systems over $1,000, trafficking of computer passwords, and modification of medical records. CFAA received its first amendment in 1994 when Congress recognized the face of computer security had drastically changed since 1984; this amendment was called the Computer Abuse Amendment Acts.
Recently, in April 2020, the Supreme Court finally reviewed the CFAA for the first time to make it more current with today’s cyber activity.
The threatscape is changing rapidly, making it very difficult to determine what to address within cyber law. Cyber laws we have today are reactionary laws, meaning something happened, then a law was developed and enacted trying to prevent it from happening again.
An example of our reactionary cyber laws is when the first significant data breach happened in 2016 when Yahoo was breached, and hackers stole around 500 million accounts dating back to 2014. This breach sparked the need for data protection. Following this breach was the Consumer Privacy Protection Act of 2017. The reaction is primarily because of the continuously changing warfare and threatscape. How can you create a law to predict something that has happened yet?
Here is a brief list of current cyber legislations:
- Health Insurance Portability and Accountability Act (HIPPA) of 1996: Designed to protect individual health records.
- Consumer Privacy Protection Act of 2017: This law was developed shortly after the large Yahoo breach in 2016 and was designed to protect customer information in an attempt to avoid identity theft.
- General Data Protection Regulation (GDPR) of 2018: This is the European Union’s most stringent privacy and security law globally, and it does have impacts on U.S. activities.
- California Consumer Privacy Act (CCPA) of 2018: This was the first U.S.specific bill passed to protect the consumer’s rights by giving them more control of personal information shared.
In recent years, the U.S. Government also used specific bills and laws to strengthen its communication and data sharing efforts.
This includes the following bills and organization:
- Cybersecurity Information Sharing Act (CISA) of 2014: CISA provides a platform for information sharing through an open-source platform while spreading cyber activity awareness.
- Cybersecurity Enhancement Act of 2014: Voluntary collaboration platform for public-private partners to improve cybersecurity through research, education, and public awareness.
- Federal Exchange Data Breach Notification Act of 2015: Requires health insurance to notify any individual whose personal data was unauthorized accessed such as a data breach.
- National Cybersecurity Protection Advancement Act of 2015: This was an amendment to the Homeland Security Act of 2002 to allow other entities such as tribal, private, and non-federal representatives within the Department of Homeland Security (DHS) National Cybersecurity and Communications Integration Center (NCCIC).
As an organization, we hope to educate, advise, and bridge the gap between Special Operations Command our congressional leaders.
This blog was written by a member of the Special Operations Association of America. These are the views and opinions of the author and are not necessarily that of the Special Operations Association of America.
Jaclyn “Jax” is a tenured Special Operations Warrant Officer, with over 17 years’ experience. She is an expert in military cyber policy and has led global development operations in cyber countermeasures to mitigate near-peer attacks. She is a tech blogger, podcaster, entrepreneur, and senior analyst in Global Intelligence. She is committed to her growth as a leader and is currently co-authoring a cybersecurity book and finishing her Master’s in Cybersecurity Risk Management at Georgetown University.